-

Encryption and Compliance: Navigating the Legal Landscape
As businesses increasingly rely on digital communication and data storage, encryption has become an important tool for maintaining compliance with various legal and regulatory requirements. One common example is the Payment Card Industry Data Security Standard (PCI DSS), which sets out requirements for the protection of credit card data. This includes the use of encryption…
-

The Importance of Encryption in Data Privacy and Cybersecurity
encryption is a vital tool for protecting sensitive information and preventing data breaches. While there may be challenges from a regulatory perspective, it is important to find a balance that allows for both privacy and public safety.
-
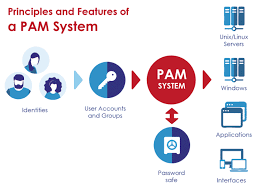
Protecting Non-Personal Accounts through Recertification
Non-personal accounts, or NPAs, are accounts that are not used by human users but rather by automated systems, services, applications, or scripts. These accounts are increasingly common in today’s digital age, as they are often used to facilitate communication and conduct business online. However, NPAs can also be vulnerable to security threats and risks if…
-

Complying with Regulations and Enhancing Security with Privileged Account Management: A Practical Guide
Privileged accounts, such as administrator or root accounts, are essential for the operation of any organization, but they also present a significant security risk if not properly managed. In this guide, we will outline best practices for managing privileged accounts in a way that not only enhances security, but also ensures compliance with relevant laws…
-
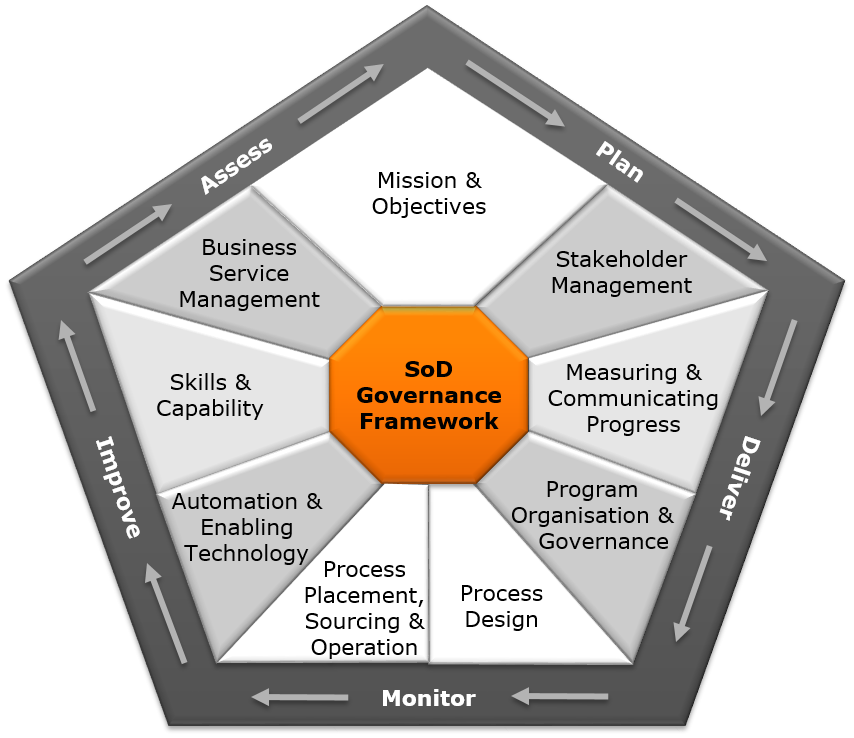
What is Segregation of Duties
A Separation of Duties (SoD) matrix is a tool used in risk management and internal controls to ensure that no one person has control over all aspects of a business process. For example, an organization might use a SoD matrix to ensure that the person who enters financial transactions into the accounting system is not…
-
Overcoming Identity Management Challenges to Boost Security and Success
Identity management is a crucial aspect of business security and success, but it can also be a major challenge. From managing multiple user accounts and passwords to protecting sensitive personal and financial information, the threat of identity theft and cyber attacks is ever-present.Fortunately, businesses can turn to skilled individuals who specialize in identity management and…

