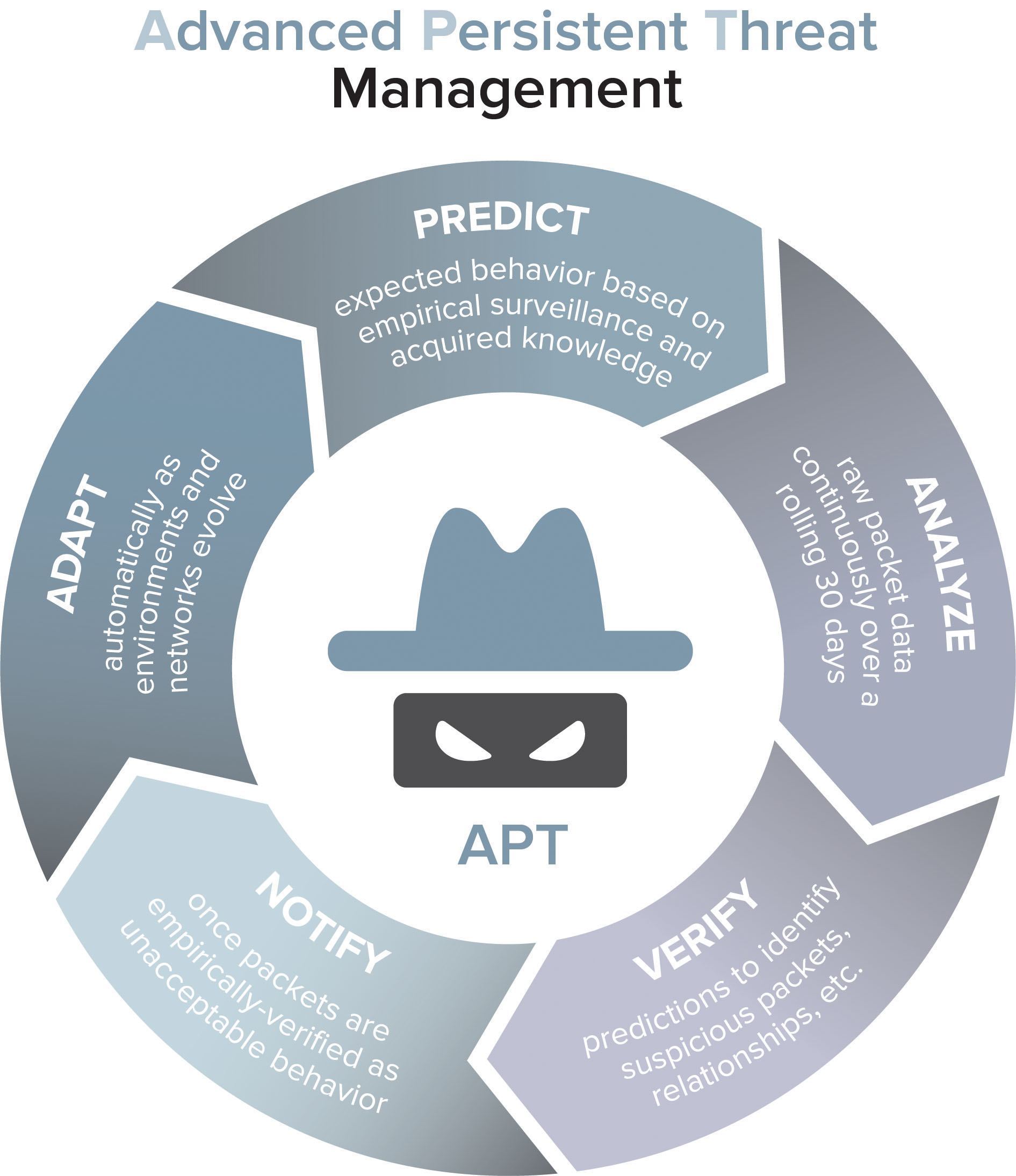
As businesses continue to adopt cloud computing technologies, the management of vulnerabilities in the cloud has become increasingly important. Vulnerabilities in the cloud can result in data breaches, financial losses, and damage to a company’s reputation. One way to efficiently manage vulnerabilities in the cloud is by using machine learning tools, such as Cloud Guard. However, relying solely on these tools is not enough. In this article, we will discuss why expert information security specialists are essential for ensuring the effective and secure use of machine learning tools in managing vulnerabilities in the cloud.
Why Expert Information Security Specialists are Essential
Machine learning tools, like Cloud Guard, are designed to continuously monitor the cloud environment and identify potential vulnerabilities in real-time. These tools use machine learning algorithms to analyze data from various sources, such as AWS Config, AWS CloudTrail, and Amazon Inspector, to identify potential vulnerabilities. While these tools can be effective in identifying vulnerabilities, they can only be as effective as the data they are provided with.
This is where expert information security specialists come in. These specialists are trained to understand the types of data that are most relevant for identifying vulnerabilities and to ensure that this data is properly collected and analyzed by the machine learning algorithms. They are also skilled at properly configuring and maintaining these tools to ensure their effectiveness.
In addition to properly configuring and maintaining machine learning tools, expert information security specialists are essential for effectively analyzing and addressing any vulnerabilities that may be identified. Machine learning tools, like Cloud Guard, can provide recommendations for remediation actions, but it is up to the information security specialist to determine the most appropriate course of action. This may involve evaluating the potential impact of the vulnerability, the likelihood of exploitation, and the resources required to address the vulnerability.
Expert information security specialists are also essential for ensuring the secure use of machine learning powered tools. These tools rely on sensitive data and access to critical systems, and it is important to have skilled professionals in place to manage these risks. Information security specialists are trained to understand the potential security implications of using machine learning tools and to implement appropriate measures to mitigate these risks.
Another reason expert information security specialists are necessary when using machine learning powered tools is that these tools are constantly evolving. Machine learning algorithms are constantly being improved and updated, and it is important to have skilled professionals in place to understand and stay up-to-date with these developments. This is especially important because the effectiveness of machine learning tools can be significantly impacted by changes to the algorithms or data sources used.
Finally, expert information security specialists are necessary when using machine learning powered tools because these tools can only provide part of the solution for managing vulnerabilities in the cloud. Information security specialists are trained to understand the broader context of vulnerability management and to implement a comprehensive approach that includes a variety of tools and strategies. This may include implementing additional security measures, such as firewalls and intrusion prevention systems, as well as implementing robust security policies and procedures.
In conclusion, expert information security specialists are essential for ensuring the effective and secure use of machine learning powered tools in managing vulnerabilities in the cloud. These specialists have the knowledge, skills, and experience necessary to properly implement, configure, and maintain these tools, as well as to effectively analyze and address any vulnerabilities that may be identified. They are also essential for ensuring the secure use of these tools and for implementing a comprehensive approach to managing vulnerabilities in the cloud. By leveraging the expertise of skilled professionals, businesses can more effectively identify and address vulnerabilities, reducing the risk of data breaches and other security incidents