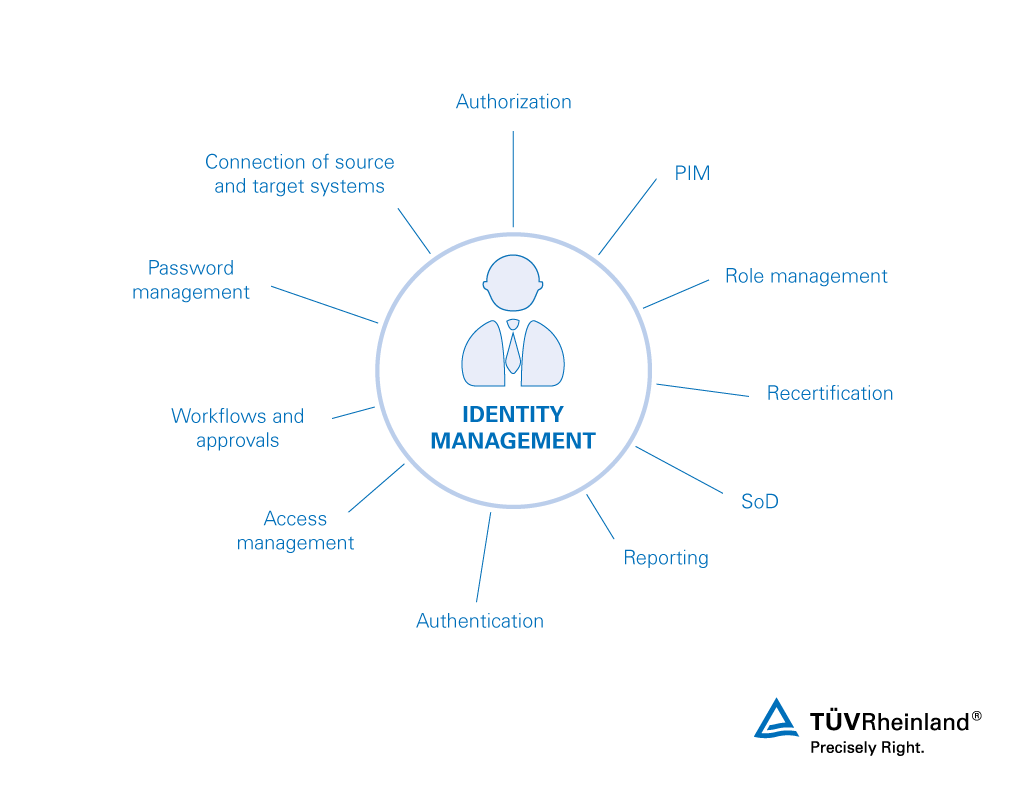
Identity and Access Management (IAM) is a critical aspect of modern businesses and organizations. It refers to the systems, processes, and policies that are put in place to manage and secure the identities and access of employees, contractors, and other stakeholders.Here are some useful tips for businesses to consider when it comes to IAM:
- Implement strong and unique passwords: One of the most important aspects of IAM is ensuring that all users have strong and unique passwords. This can help to prevent unauthorized access and protect against password-based attacks. Consider implementing a password policy that requires users to create passwords that are at least 8 characters long, contain a mix of letters, numbers, and special characters, and are changed regularly.
- Use multi-factor authentication: Multi-factor authentication (MFA) adds an extra layer of security to user accounts by requiring additional information beyond a username and password to verify a user’s identity. This can include a code sent to a phone, a biometric scan, or a security token. Implementing MFA can help to prevent unauthorized access to sensitive systems and data
- Set up role-based access controls: Role-based access controls allow you to grant users access to only the resources and systems that are relevant to their job duties. This can help to prevent accidental or intentional misuse of sensitive data and systems.
- Monitor user activity: Regularly monitoring user activity can help you to identify any unusual or suspicious activity and take appropriate action. This can include setting up alerts for certain types of activity, such as logging in from a new location or accessing sensitive data.
- Conduct regular audits and reviews: It’s important to regularly review and audit your IAM systems and policies to ensure that they are effective and up to date. This can include reviewing access controls, evaluating the strength of passwords, and checking for any unauthorized access
By following these tips, businesses can help to ensure that their IAM systems are secure and effective in protecting sensitive data and systems. By taking a proactive approach to IAM, businesses can protect themselves and their stakeholders from potential security threats.