-
Protecting Non-Personal Accounts through Recertification
Non-personal accounts, or NPAs, are accounts that are not used by human users but rather by automated systems, services, applications, or scripts. These accounts are increasingly common in today’s digital age, as they are often used to facilitate communication and conduct business online. However, NPAs can also be vulnerable to security threats and risks if…
-

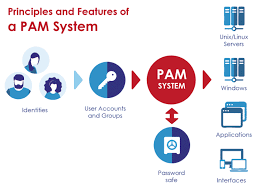
Complying with Regulations and Enhancing Security with Privileged Account Management: A Practical Guide
Privileged accounts, such as administrator or root accounts, are essential for the operation of any organization, but they also present a significant security risk if not properly managed. In this guide, we will outline best practices for managing privileged accounts in a way that not only enhances security, but also ensures compliance with relevant laws…
-

Maximizing Security and Efficiency with Privileged Account Management: A Practical Guide
Privileged accounts, such as administrator or root accounts, are critical to the operation of any organization. However, they also represent a significant security risk if not properly managed. In this study, we will explore best practices for managing privileged accounts in a secure and efficient manner. Privileged accounts, such as administrator or root accounts, are…
-
5 Essential Tips for Strengthening Your Business’s Identity and Access Management
Identity and Access Management (IAM) is a critical aspect of modern businesses and organizations. It refers to the systems, processes, and policies that are put in place to manage and secure the identities and access of employees, contractors, and other stakeholders.Here are some useful tips for businesses to consider when it comes to IAM: By…
-

5 Practical Tips for Protecting Your Business from Cyber Attacks
Cyberattacks are a growing threat for businesses of all sizes. According to a report from Cybersecurity Ventures, the cost of cybercrime is expected to reach $6 trillion annually by 2021. To protect your business from these types of attacks, it is important to take a proactive approach to cybersecurity. In this blog post, we will…
-
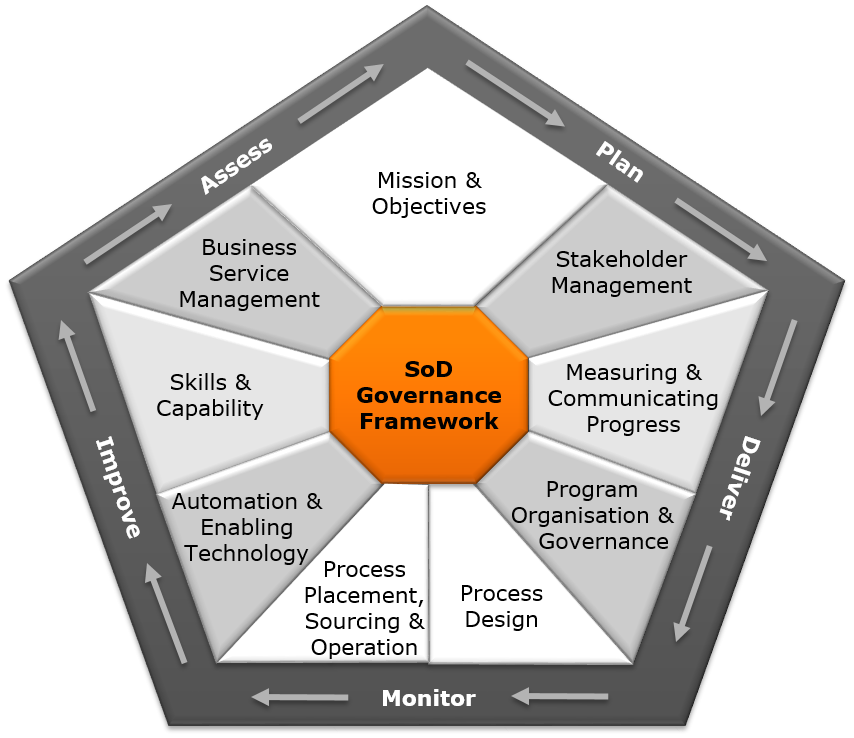
What is Segregation of Duties
A Separation of Duties (SoD) matrix is a tool used in risk management and internal controls to ensure that no one person has control over all aspects of a business process. For example, an organization might use a SoD matrix to ensure that the person who enters financial transactions into the accounting system is not…
-
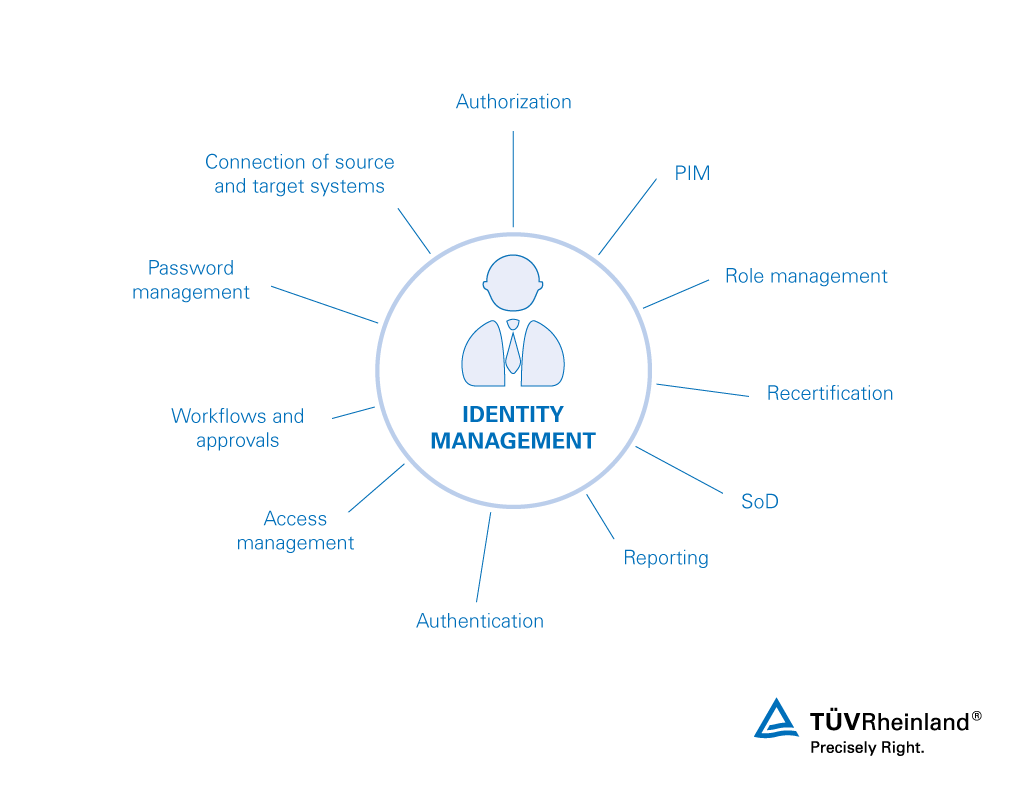
Overcoming Identity Management Challenges to Boost Security and Success
Identity management is a crucial aspect of business security and success, but it can also be a major challenge. From managing multiple user accounts and passwords to protecting sensitive personal and financial information, the threat of identity theft and cyber attacks is ever-present.Fortunately, businesses can turn to skilled individuals who specialize in identity management and…

