-
The Cost of Cyber Attacks: Statistics and Impact on Businesses
According to a report from cybersecurity firm McAfee, the global cost of cyberattacks reached $1 trillion in 2019. This is an alarming statistic, as it shows the significant impact that these attacks can have on businesses of all sizes. One of the most costly impacts of a cyberattack is the loss of data. A study…
-
Encryption in the Cloud: Challenges and Best Practices
As more and more businesses move their data and applications to the cloud, encryption has become an important consideration for ensuring the security and privacy of this sensitive information. One key challenge in the cloud is the need to balance security and convenience. Encrypting data in the cloud can make it more difficult to access,…
-

The Basics of Encryption: How It Works and Why It’s Important
If you’ve ever used a password to access an online account or sent a secure email, you’ve likely encountered encryption. But what exactly is encryption and why is it so important? Encryption is a way of encoding data so that it can only be accessed by someone with the proper decryption key. It’s used to…
-

The Importance of Encryption in Data Privacy and Cybersecurity
encryption is a vital tool for protecting sensitive information and preventing data breaches. While there may be challenges from a regulatory perspective, it is important to find a balance that allows for both privacy and public safety.
-
Protecting Non-Personal Accounts through Recertification
Non-personal accounts, or NPAs, are accounts that are not used by human users but rather by automated systems, services, applications, or scripts. These accounts are increasingly common in today’s digital age, as they are often used to facilitate communication and conduct business online. However, NPAs can also be vulnerable to security threats and risks if…
-

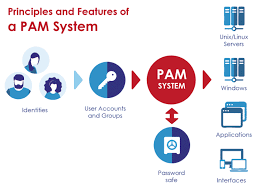
Maximizing Security and Efficiency with Privileged Account Management: A Practical Guide
Privileged accounts, such as administrator or root accounts, are critical to the operation of any organization. However, they also represent a significant security risk if not properly managed. In this study, we will explore best practices for managing privileged accounts in a secure and efficient manner. Privileged accounts, such as administrator or root accounts, are…
-
The Importance of Network Security Monitoring
According to a report by cybersecurity firm FireEye, the average time to detect a breach is 99 days. This highlights the importance of continuous monitoring to ensure that threats are detected and addressed as quickly as possible.
-
10 Questions to get you started in designing or improving your Information Security Management System
An ISMS, or information security management system, is a framework that helps organizations ensure the confidentiality, integrity, and availability of their information assets. 10 questions to help you design yours !
-

The Importance of Network Security Policies
Having a written security policy can significantly reduce the risk of a data breach.
-

The Growing Threat of Ransomware: Statistics and Prevention Tips
Ransomware is a type of cyberattack that involves hackers holding a company’s data hostage until a ransom is paid. According to a report from cybersecurity firm Symantec, ransomware attacks increased by 36% in 2020. One of the reasons for the increase in ransomware attacks is the growing use of cloud-based storage. A survey by Barracuda…

