-

5 Practical Tips for Protecting Your Business from Cyber Attacks
Cyberattacks are a growing threat for businesses of all sizes. According to a report from Cybersecurity Ventures, the cost of cybercrime is expected to reach $6 trillion annually by 2021. To protect your business from these types of attacks, it is important to take a proactive approach to cybersecurity. In this blog post, we will…
-
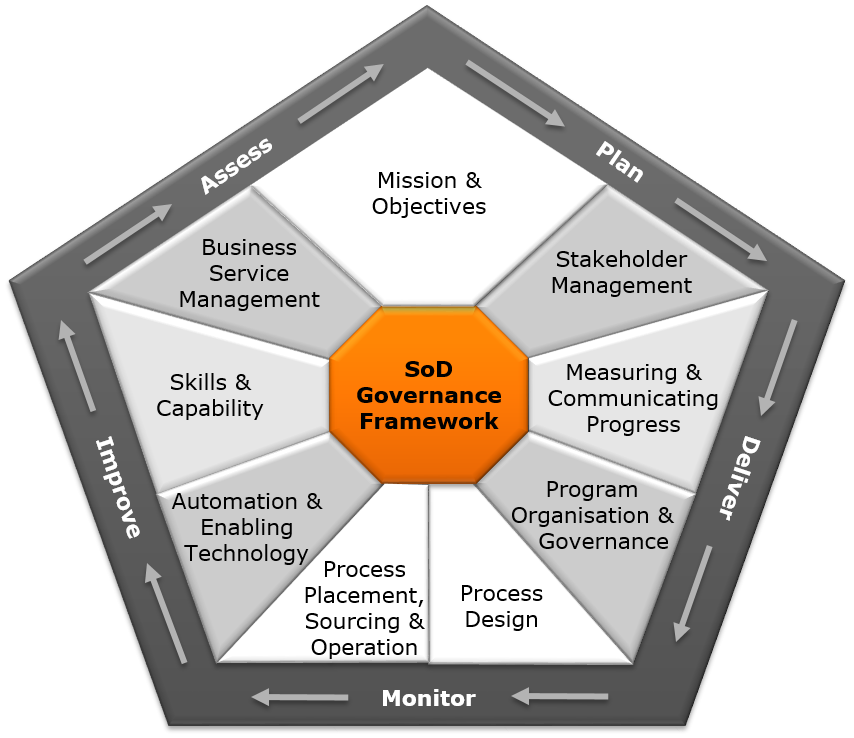
What is Segregation of Duties
A Separation of Duties (SoD) matrix is a tool used in risk management and internal controls to ensure that no one person has control over all aspects of a business process. For example, an organization might use a SoD matrix to ensure that the person who enters financial transactions into the accounting system is not…
-
Talent Acquisition : Think out of the box
We were invited at EVANTA recently and discussed the recurring issue of talent acquisition and skills shortage. One recurring issue faced by CISOs is how to acquire talented people in information security. To put it bluntly, we believe in recruiting and training talents out of the box and based on real skills rather than relying…
-

Machine Learning & Advanced Persistent Threats
Machine learning has the potential to revolutionize the way we tackle advanced persistent threats (APTs). These threats, which often come from state-sponsored hackers or organized crime groups, can be incredibly difficult to detect and stop. Traditional security tools and techniques are often ineffective against APTs, which are designed to evade detection and continue operating for…
-
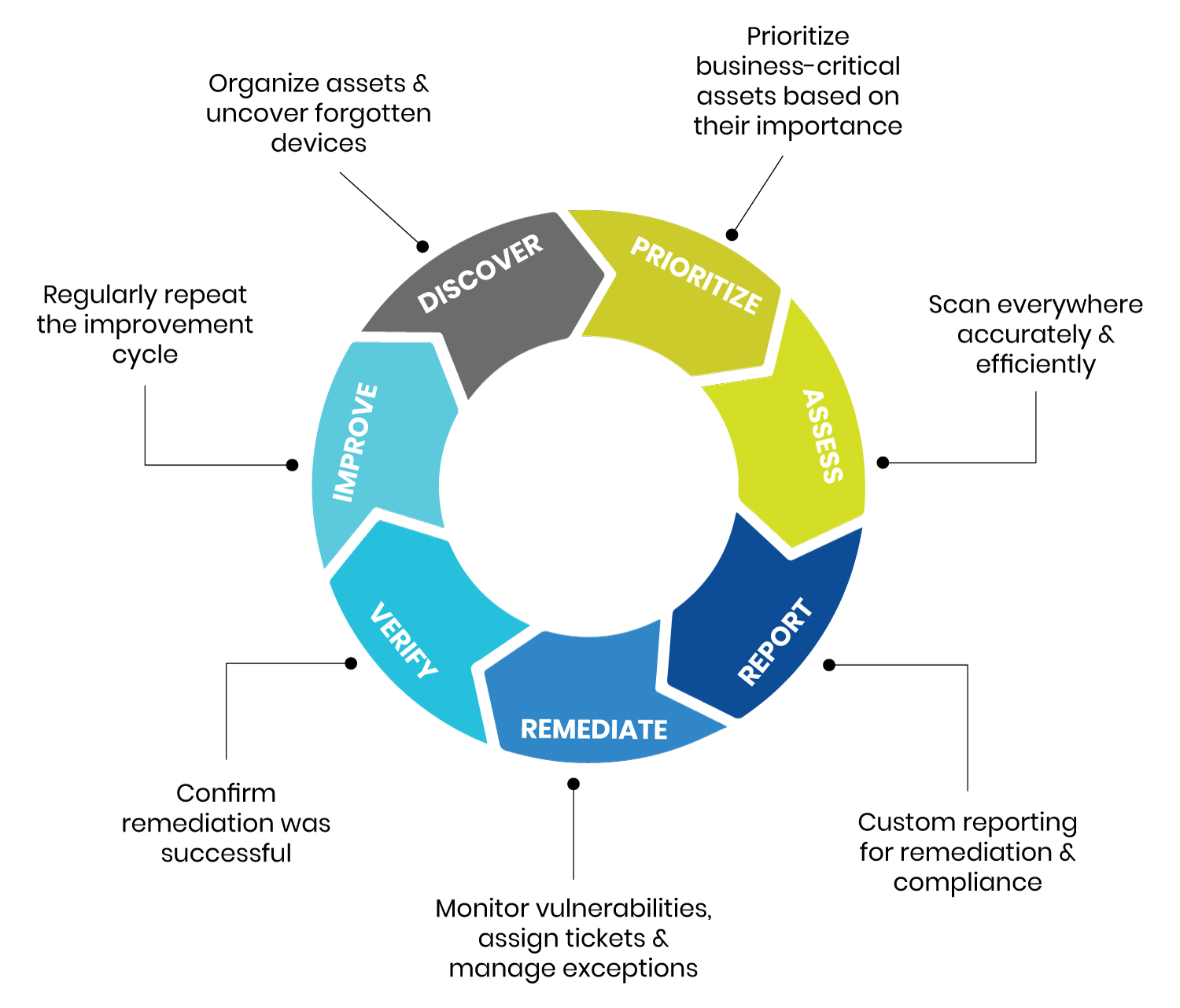
The challenges of managing vulnerabilities
Vulnerabilities management is a crucial aspect of cybersecurity, as it involves identifying, assessing, and addressing vulnerabilities in computer systems and networks. However, it can be a challenging task for several reasons.Firstly, the sheer volume of vulnerabilities can be overwhelming. With new vulnerabilities being discovered every day, it can be difficult for organizations to keep up…
-

Information Security & your business!
Information security is a crucial concern for businesses of all sizes and industries. As the amount of sensitive data and the number of cyber threats continue to increase, it’s essential to implement robust security measures to protect your organization and its assets. One critical aspect of information security is identity management. This refers to the…
-
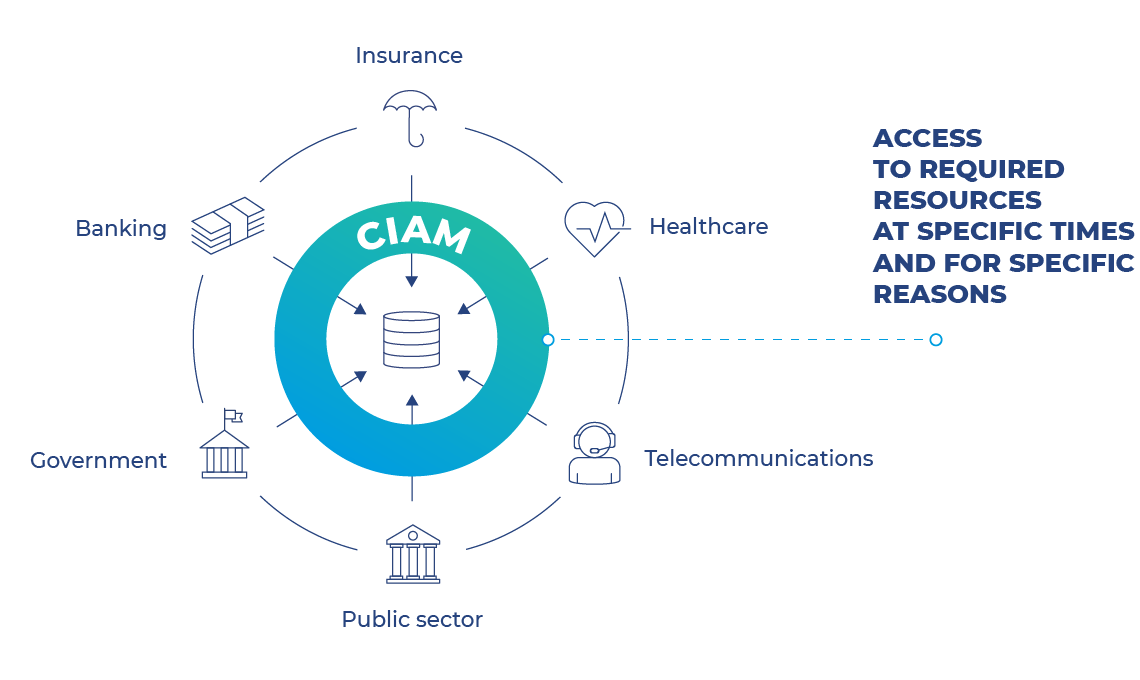
Overcoming Identity Management Challenges to Boost Security and Success
Identity management is a crucial aspect of business security and success, but it can also be a major challenge. From managing multiple user accounts and passwords to protecting sensitive personal and financial information, the threat of identity theft and cyber attacks is ever-present.Fortunately, businesses can turn to skilled individuals who specialize in identity management and…

