-
The Cost of Cyber Attacks: Statistics and Impact on Businesses
According to a report from cybersecurity firm McAfee, the global cost of cyberattacks reached $1 trillion in 2019. This is an alarming statistic, as it shows the significant impact that these attacks can have on businesses of all sizes. One of the most costly impacts of a cyberattack is the loss of data. A study…
-
Encryption in the Cloud: Challenges and Best Practices
As more and more businesses move their data and applications to the cloud, encryption has become an important consideration for ensuring the security and privacy of this sensitive information. One key challenge in the cloud is the need to balance security and convenience. Encrypting data in the cloud can make it more difficult to access,…
-

Encryption and Compliance: Navigating the Legal Landscape
As businesses increasingly rely on digital communication and data storage, encryption has become an important tool for maintaining compliance with various legal and regulatory requirements. One common example is the Payment Card Industry Data Security Standard (PCI DSS), which sets out requirements for the protection of credit card data. This includes the use of encryption…
-

The Basics of Encryption: How It Works and Why It’s Important
If you’ve ever used a password to access an online account or sent a secure email, you’ve likely encountered encryption. But what exactly is encryption and why is it so important? Encryption is a way of encoding data so that it can only be accessed by someone with the proper decryption key. It’s used to…
-
The Future of Encryption: Quantum Computing and Post-Quantum Cryptography
In recent years, there has been a lot of buzz around the potential of quantum computing and its potential impact on encryption. Quantum computers, which use the principles of quantum mechanics to perform calculations, have the potential to significantly increase the speed and power of computation. This has led to concerns that quantum computers could…
-

The Importance of Encryption in Data Privacy and Cybersecurity
encryption is a vital tool for protecting sensitive information and preventing data breaches. While there may be challenges from a regulatory perspective, it is important to find a balance that allows for both privacy and public safety.
-
Protecting Non-Personal Accounts through Recertification
Non-personal accounts, or NPAs, are accounts that are not used by human users but rather by automated systems, services, applications, or scripts. These accounts are increasingly common in today’s digital age, as they are often used to facilitate communication and conduct business online. However, NPAs can also be vulnerable to security threats and risks if…
-

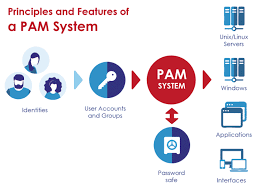
Complying with Regulations and Enhancing Security with Privileged Account Management: A Practical Guide
Privileged accounts, such as administrator or root accounts, are essential for the operation of any organization, but they also present a significant security risk if not properly managed. In this guide, we will outline best practices for managing privileged accounts in a way that not only enhances security, but also ensures compliance with relevant laws…
-

Maximizing Security and Efficiency with Privileged Account Management: A Practical Guide
Privileged accounts, such as administrator or root accounts, are critical to the operation of any organization. However, they also represent a significant security risk if not properly managed. In this study, we will explore best practices for managing privileged accounts in a secure and efficient manner. Privileged accounts, such as administrator or root accounts, are…
-
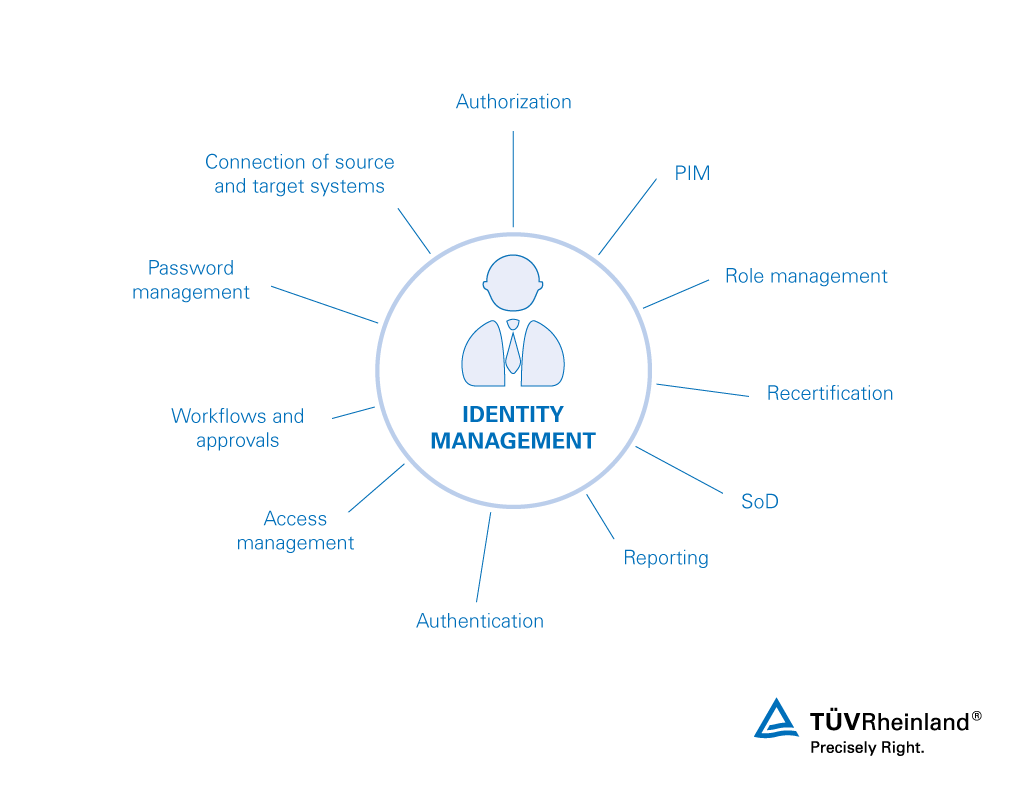
5 Essential Tips for Strengthening Your Business’s Identity and Access Management
Identity and Access Management (IAM) is a critical aspect of modern businesses and organizations. It refers to the systems, processes, and policies that are put in place to manage and secure the identities and access of employees, contractors, and other stakeholders.Here are some useful tips for businesses to consider when it comes to IAM: By…

