-
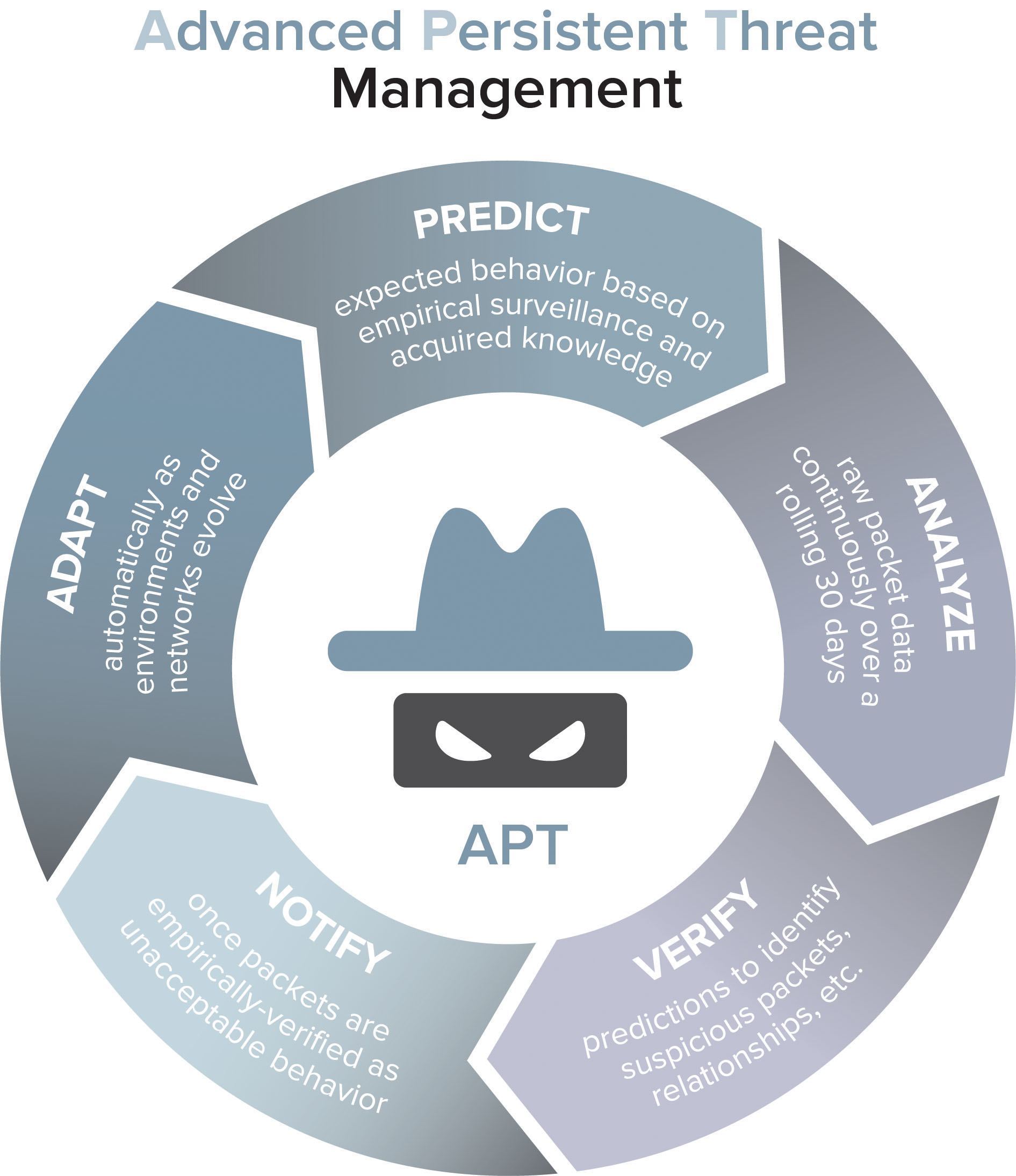
The Importance of Expert Information Security Specialists in Managing Vulnerabilities in the Cloud
As businesses continue to adopt cloud computing technologies, the management of vulnerabilities in the cloud has become increasingly important. Vulnerabilities in the cloud can result in data breaches, financial losses, and damage to a company’s reputation. One way to efficiently manage vulnerabilities in the cloud is by using machine learning tools, such as Cloud Guard.…
-
The Importance of Network Security Monitoring
According to a report by cybersecurity firm FireEye, the average time to detect a breach is 99 days. This highlights the importance of continuous monitoring to ensure that threats are detected and addressed as quickly as possible.
-
The Importance of Network Segmentation in Cybersecurity
Network segmentation is the practice of dividing a network into smaller, isolated segments in order to improve security and reduce the risk of a data breach. According to a report by the National Institute of Standards and Technology (NIST), network segmentation can significantly reduce the impact of a cyberattack. One of the key benefits of…
-
10 Questions to get you started in designing or improving your Information Security Management System
An ISMS, or information security management system, is a framework that helps organizations ensure the confidentiality, integrity, and availability of their information assets. 10 questions to help you design yours !
-

The Importance of Network Security Policies
Having a written security policy can significantly reduce the risk of a data breach.
-

The Growing Threat of Ransomware: Statistics and Prevention Tips
Ransomware is a type of cyberattack that involves hackers holding a company’s data hostage until a ransom is paid. According to a report from cybersecurity firm Symantec, ransomware attacks increased by 36% in 2020. One of the reasons for the increase in ransomware attacks is the growing use of cloud-based storage. A survey by Barracuda…

